Network Vulnerability Assessment And Penetration Testing
As a result, it was highly vital to scan Internet-facing access points to disclose the safety weaknesses in the network. When the scanning was over, the network susceptability evaluation "draft" outcomes were correlated with versioning and also fingerprinting details to far better examine running services. Afterwards, the safety and security designers performed hand-operated confirmation of the scanner results to remove the variety of incorrect positives.
The security team gave the organization with a report having the list of vulnerabilities, stating their severity level (reduced, tool or high) and also defining restorative procedures to reduce risks. The safety and security engineers paid the customer's attention to the crucial ones that required to be chosen a first-priority basis so that the consumer came to be ready for PCI DSS validation.
This sort of cybersecurity attacks suggested that enemies might eavesdrop on the communication in between two legitimately communicating hosts. When efficiently accomplished, such assaults might permit intruders to acquire delicate info, such as verification credentials. Network vulnerability analysis is typically followed by penetration screening. There's no usage in performing infiltration testing before the discovered susceptabilities are patched, as the objective of penetration screening is not simply attempting to obtain into the network but likewise taking a look at the network environment 'with a brand-new collection of eyes' after the renovations are made.
Internal Network Vulnerability Assessment
Although both infiltration testing and also vulnerability analysis can be black box, white box or grey box, there are significant distinctions between these 2 procedures. For instance, while vulnerability analysis concentrates on revealing as many security weaknesses as feasible, infiltration test means trying to get in the network as deep as feasible ("the deepness over breadth approach").
Vulnerability analysis is not a panacea, but it's one of the designed to stop networks from being hacked by making use of susceptabilities in them because it enables concentrating on the essential properties of the network atmosphere as well as exposing the weaknesses in it. For a company thinking about securing their safety and organization online reputation, cybersecurity scientists advise to welcome all the chances readily available to make certain that your network framework is shielded effectively to resist the trespassers' stress.
On a regular basis scheduled network vulnerability scanning can aid a company recognize weaknesses in their network security before the bad men can place an attack. The goal of running a susceptability scanner or carrying out an external vulnerability analyses is to determine devices on your network that are open to known susceptabilities without in fact compromising your systems.
The Art Of Network Vulnerability Assessment
Performing periodic susceptability scans is the excellent enhance to performing normal anti-viruses updates and applying the essential security spots for any kind of brand-new vital susceptability found.
The general goal of a Susceptability Evaluation is to check, examine, assess and also report on the level of risk related to any protection vulnerabilities found on the public, internet-facing tools as well as to provide your company with appropriate mitigation techniques to deal with those found susceptabilities.
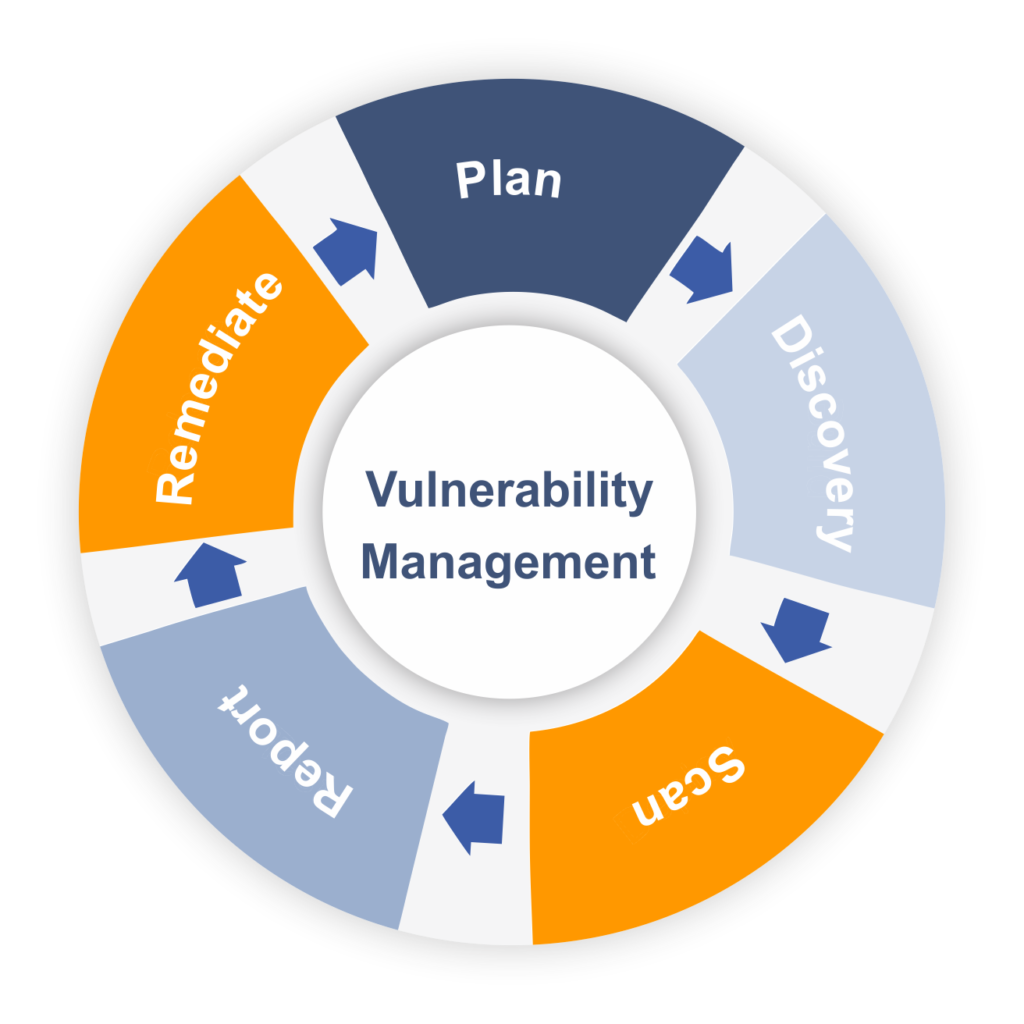
Network Vulnerability Assessment
In today's risk environment, it's not simply an excellent concept to conduct a cybersecurity vulnerability evaluation, as well as to do so on a regular basis it's a core demand for any company that intends to safeguard critical data and also make sure that its networks as well as systems aren't subjected to cyberattacks. Falling short to do so can, put simply, spell the end of your company.
Renub Research expects the international susceptability evaluation market to reach $15 billion by 2024, attributing the anticipated development to several aspects, consisting of raised cloud adoption, the expanding threat of data theft, as well as a surge in the variety of systems affected by regulative needs.
Network Vulnerability Assessment And Penetration Testing
The information collected via susceptability screening can be leveraged Dallas IT services by IT as well as security groups to evaluate and boost your hazard mitigation and avoidance procedures. It includes determining the systems on your network (including evaluating which are most useful as well as crucial), recognizing and also racking up any type of susceptabilities found on those systems, and prioritizing the removal procedure to focus on the greater risk vulnerabilities that influence your most important systems.
You can't fix the defects you can't see and also the clearer your feeling of your overall protection pose, the much better located you are to enhance it. Conducting susceptability evaluations on a routine basis can place you one step in advance of the poor individuals, identify holes in your protection defenses yourself as opposed to waiting on them to be subjected by a violation, and can help you connect holes in your own security prior to hazard stars discover them.
A susceptability analysis can likewise offer even more detailed and also actionable information than may be readily available from a violation and also attack simulation (BAS) device, which automates the procedure of running substitute assaults on your systems to test your protection posture. In several means, BAS tools serve a different function from susceptability assessments, and the two can work well in tandem to enhance your general safety.